Introduction
iPhones have a reputation for robust security, largely thanks to the extensive hardware security features they incorporate. As one of the world’s most widely-used and secure mobile operating systems, iOS consistently attracts the attention of hackers. A notable example of this is the sophisticated ‘Operation Triangulation’ attack discovered by Kaspersky. With each new version, Apple intensifies the security protocols within iOS, making it increasingly challenging for attackers to discover vulnerabilities. Consequently, the nature of these attacks is evolving, becoming more intricate and advanced in response to the heightened security measures.
Despite the robust security measures in iOS, a recent vulnerability was identified in a kernel extension known as CoreTrust. CoreTrust’s role parallels that of AppleMobileFileIntegrity (AMFI), which is to verify the signatures of executable files. Essentially, when an attempt is made to run an unsigned binary executable, the dynamic linker (dyld) typically returns an error, specifically error 85, indicating a 85 EBADEXEC Bad executable (or shared library).
This vulnerability in CoreTrust, designated as CVE-2022-26766, impacted several iOS versions. It was first addressed in iOS 15.5, but the issue resurfaced in the betas of iOS 15.6 before being rectified again in the final release. This bug allowed the bypassing of CoreTrust’s security checks, enabling unauthorized software execution. iOS versions prior to 12 did not have CoreTrust and hence were not affected by this bug. The regression of this bug did not impact iOS 12 and 13. However, versions 15.0 to 15.4.1 were susceptible to the original CoreTrust bug, leading to its exploitation in applications such as TrollStore. Later versions, including iOS 15.5 to 16.6.1 and iOS 17.0, also encountered an AMFI/CoreTrust issue, where the system failed to adequately verify the legitimacy of a root certificate used to sign a binary. These incidents underline the complexity and evolving challenges in maintaining iOS security.
The SeaShell Framework, created by EntySec, serves as a demonstrative model for a potential attack method that hackers could employ to install malicious software on devices. This method circumvents security protocols by exploiting the CoreTrust vulnerability. To raise awareness about the viability of such attacks in the current digital landscape, EntySec has released all the relevant code associated with this attack process. This information is particularly valuable to the public and security experts. It is important to note that applications like the previously mentioned TrollStore could act as an initial step in such an attack. Further details on this aspect will be provided subsequently.
SeaShell Framework
SeaShell Framework is an iOS post-exploitation framework that enables you to access the device remotely, control it and extract sensitive information. All attacker needs to do is generate IPA file and start TCP listener. The IPA needs to be installed trough TrollStore or other application that exploits CoreTrust bug and launched single time. After this, if listener and connect-back host were configured correctly, attacker will receive an interactive session with the device. Moreover, SeaShell utilizes a sophisticated payload called Pwny. It has lots of features including evasion, TLS encryption, dynamic extensions and much more. There are all the features that SeaShell provides:
- IPA generator - All you need to do is generate an IPA file and install it on a target’s device via TrollStore or other IPA installer that bypasses CoreTrust. After app was installed, a target simply need to run an app single time (he may close application completely after this).
- Powerful Implant - SeaShell Framework uses the advanced and powerful payload with lots of features. It is called Pwny. You can extend it by adding your own post-exploitation modules or plugins.
- Basic Set - SeaShell Framework comes with basic set of post-exploitation modules that may exfiltrate following user data: SMS, VoiceMail, Safari history and much more.
- Encrypted communication - Communication between device and SeaShell is encrypted using the TLS 1.3 encryption by default.
- Regular updates - SeaShell Framework is being actively updated, so don’t hesitate and leave your feature request!
It can be installed for publicly available repository using pip and then the interface might be launched with seashell command:
pip3 install git+https://github.com/EntySec/SeaShell
It then may be updated with this command:
pip3 install --force-reinstall git+https://github.com/EntySec/SeaShell
How IPA works
So, basically IPA is a compressed application bundle for iOS application that contains main executable, icons, Info.plist and other files related to the program. SeaShell utilizes its own application bundle with a simple executable and other executable which launches the Pwny payload. These are the stages of attack:
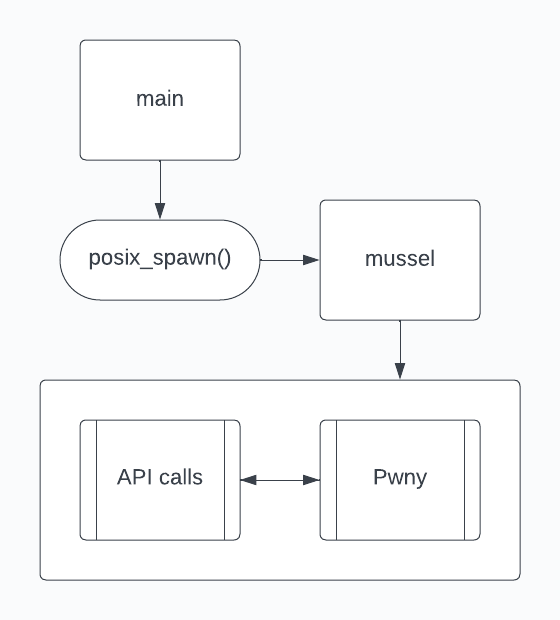
Usage
Generating IPA
Simply generate custom IPA file or patch existing one and install it on target’s iPhone or iPad via TrollStore or other IPA installer that bypasses CoreTrust.
Starting listener
Then you will need to start a listener on a host and port you added to your IPA. Once the installed application opens, you will receive a connection.
Accessing device
Once you have received the connection, you will be able to communicate with the session through a Pwny interactive shell. Use devices -i <id> to interact and help to view list of all available commands. You can even extract Safari history like in the example below.
Interactive shell
The interactive shell offered by Pwny simplifies the process of interacting with a compromised device. It features a robust interface equipped with essential tools for various tasks, such as managing the file system, extracting confidential data, uploading files, running programs, and many more capabilities. Below, I have outlined some of the prominent features that are presently available in this interface.
Safari data
At present, it’s possible to extract sensitive data from Safari using a few commands. To access the web browsing history, the command safari_history can be used. This command retrieves the database located at /var/mobile/Library/Safari/ and parses it for information. Similarly, the command safari_bookmarks operates in the same manner, allowing you to view saved bookmarks by downloading and parsing the relevant Safari data.
SMS data
The interface also grants access to SMS data. You can list the chats present in the SMS application using the command sms -l. To extract the chat history with a specific contact, the command sms <recipient> can be used. Additionally, the contacts command allows for the retrieval of the contact list from the address book.
Hooking to other applications
Interface provides its own persistence method. Since on non-jailbroken phones (and rootless) launchctl is useless, interface uses “hooking”. This means that payload is being injected inside a desired application’s bundle and next time application is launched, attacker gets new remote connection. The hook can be installed via hook command and removed via unhook. Below I install hook to Calculator.app:
Media player
A fun feature that I would like to introduce is player command. It enables you to control media player. It has few options that are listed below.
-
player info- Get current playing item information. -
player pause- Stop current playing item. -
player play- Resume current playing item. -
player next- Go to next playing item. -
player back- Go back to the previous playing item. -
player wave <file>- Play local audio file on device. (known supported formats arewavandmp3)
How to protect?
In response to numerous online requests, I’ve prepared a guide on how to reduce the likelihood of falling victim to an attack via the SeaShell framework. Below are my suggestions:
- 1. Unzip IPA file that you want to install.
-
2. Check of suspicious executables in the application bundle (e.g. SeaShell Framework adds executable called
musselto its application bundle which is a representation of Pwny payload). -
3. Read
Info.plistand search for suspicious entries (e.g. SeaShell addsCFBundleBase64Hashto itsInfo.plist, it contains a host pair<host>:<port>encoded with base64) - 4. Check MD5 hash sum of the file to check its integrity.
Conclusion
The SeaShell Framework serves as a stark reminder that iOS security flaws can be exploited for purposes beyond just sideloading applications or jailbreaking, as seen with TrollStore. These vulnerabilities can also be used to install harmful software onto devices. This highlights the importance of vigilance when handling IPA packets. Before installing any IPA packet on your system, it’s crucial to thoroughly analyze it for potential security risks. This extra step of caution can help prevent the inadvertent installation of malicious software, safeguarding your device from unwanted breaches and ensuring the integrity of your system’s security.